Corporate and public America has been the victim of more than its fair share of major cyber attacks in recent months – from the high profile ransomware attack on the Colonial Pipeline in May, to the hack targeting Kaseya (and ultimately spreading through thousands of corporate networks using its software) in July. Worryingly, an increasing number of these attacks have been targeting assets of national importance, such as the notorious attack on SolarWinds, through which hackers were able to spy on organisations including the Department of Homeland Security and the Treasury Department.
It has been suggested that one of the (admittedly many) reasons for the targeting of US institutions is a lacking regulatory framework. Whilst other parts of the developed world have already put in place, or are developing, enhanced regulatory frameworks to require important institutions to respond effectively to cyber attacks (and thereby, encouraging those institutions to invest more in cyber defences), the patchwork regulatory landscape in the US has not encouraged consistency in cyber capabilities across the board. This creates vulnerability gaps, or ‘weak links’, in the cyber chain that hackers are ready and willing to exploit.
It seems, though, that US politicians may have had enough. In a display of bipartisan effort, Democratic Senator Mark Warner and Republican Senators Marco Rubio and Susan Collins have tabled (as a bill) the Cyber Incident Notification Act of 2021 (CINA), pursuant to which federal agencies, government contractors and critical infrastructure owners and operators would be required to notify the US federal government within 24 hours of experiencing a cyber attack. Once notified, the intention is that the US government would then be able to mobilise to protect critical industries across the country. To incentivise information sharing, the proposal is that affected organisations would be granted limited immunity, and the US government would be required to implement data protection procedures to anonymise personal information and safeguard privacy.
While the CINA is the first proposed law of its kind in the US, it is not unique globally. Back in July 2016, the European Union issued its Directive (EU) 2016/1148 on Security of Network and Information Systems (NIS Directive). More recently, on 9 November 2020 Australia tabled the Security Legislation Amendment (Critical Infrastructure) Bill (2020) (the Critical Infrastructure Bill) which is still subject to review by the Parliamentary Joint Committee on Intelligence and Security (the Committee heard oral submissions from industry participants in July). (For more information on the Critical Infrastructure Bill, click here). Together, we refer to these three laws as the Critical Infrastructure Laws.
This article details some of the key obligations in the CINA, and looks at how these align with the requirements under the NIS Directive and the Critical Infrastructure Bill. The most important obligation in the CINA relates to the mandatory reporting of cyber incidents; we look at how the mandatory reporting obligations in the three Critical Infrastructure Laws compare, in addition to considering the more general mandatory data breach notification provisions under the Privacy Act 1988 (Cth) (the Privacy Act). To conclude, we provide some thoughts on why the CINA may be relevant to Australian companies, and set out the anticipated timeline for its passage.
Key Requirements under the Critical Infrastructure Laws
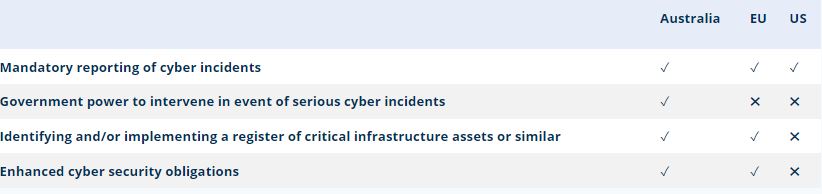
The following table sets out the key requirements under each of the Critical Infrastructure Laws. Note that the laws in Australia and the US are not yet settled and, therefore, the requirements may still change as a result of industry consultation or the legislative process.
What the above table demonstrates, at a glance, is that whilst the Critical Infrastructure Laws all ultimately seek to achieve the same end (i.e. to improve the overall cyber security of the relevant nation with a focus on critical infrastructure assets), the scope of each law is quite different. The Australian law (as currently proposed) is by some distance the most far-reaching, with the US law adopting a relatively narrow focus on reporting of incidents only.
Mandatory Reporting Requirements under the Critical Infrastructure Laws
Whilst each of the Critical Infrastructure Laws approaches ensuring the cyber-security of critical infrastructure assets in different ways, they each contain a baseline requirement on affected organisations to notify relevant government authorities upon the occurrence of a cyber-attack.
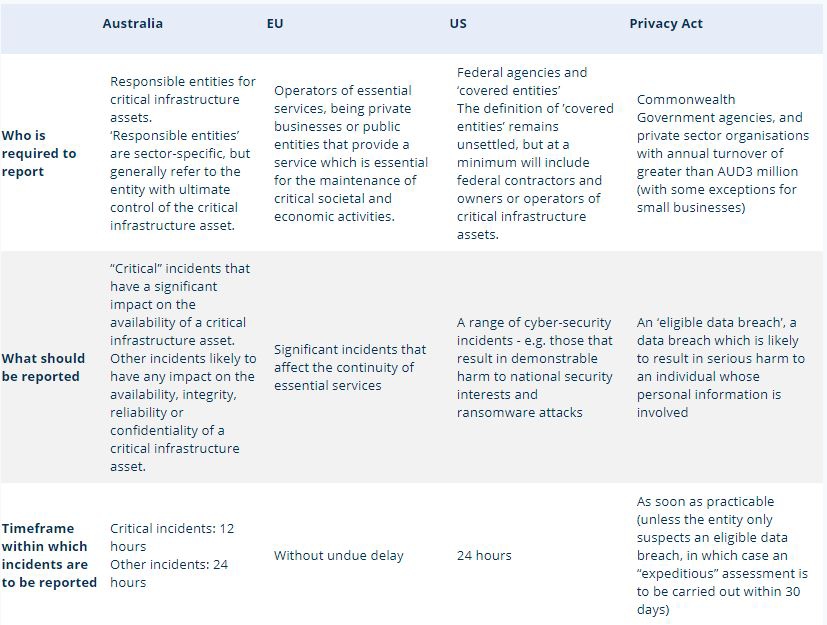
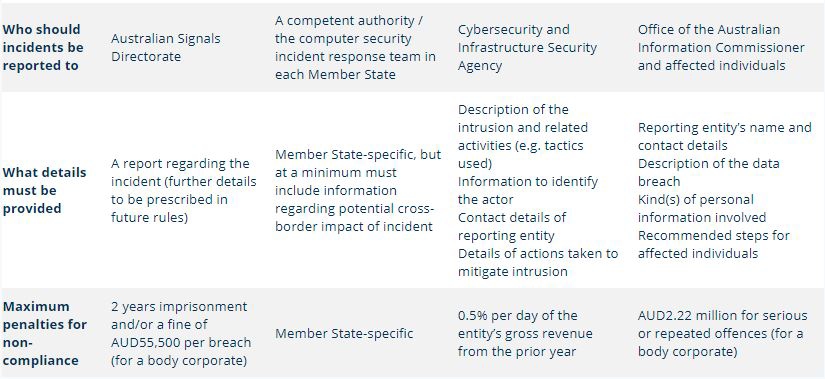
The table below compares the mandatory reporting requirements in each of the Critical Infrastructure Laws. In Australia, organisations may separately be subject to mandatory data breach notification obligations under the Privacy Act (for more information, click here), as well as under sector-specific laws and regulations. For completeness, the table below also summarises the key obligations under the Privacy Act notification scheme.
It is important to note that in the context of the Critical Infrastructure Bill, the mandatory notification requirements (and, in particular, the timeframes within which notifications must be made) have been the subject of intense industry scrutiny and comment – with a number of organisations pushing for an extension of the timeframes to 72-plus hours. As a result of this industry feedback, it is possible that the requirements in the Critical Infrastructure Bill may change before they become law.
What next?
Whilst the CINA appears to have broad bipartisan support in the US Senate, it is still in its infancy and it is unlikely that a final version will make its way through the legislative process and into law this year.
However, a number of recent developments in the US indicate that this is a legislative priority for the Biden government, and that the CINA may be pushed through more quickly than expected. On 28 July, the White House released a national security memorandum directing two federal agencies to develop and issue cybersecurity performance goals for critical infrastructure sectors. On the same day, President Biden issued an Executive Order aimed at preventing cyber-attacks on America’s critical infrastructure. Concurrent discussions within the Senate around how to better prevent and respond to ransomware attacks in the US, as well as the release of a joint cybersecurity advisory memo that highlights the top vulnerabilities exploited by malicious cyber actors, all demonstrate how important cyber readiness is to US State security.
Why is this relevant to Australian organisations?
New developments such as these add to an already substantial, and increasingly complex, regulatory landscape that businesses need to comply with.
Any Australian businesses that operate in the US in the critical infrastructure sector (either as suppliers, subcontractors or owners and operators) will need to be aware of the requirements of the CINA, as will Australian businesses engaging with US-based suppliers or contractors who are subject to the obligations (and who may look to flow these down into the contractual arrangements with the Australian business).
What is apparent is that organisations that operate globally will increasingly find themselves faced with a matrix of different compliance obligations, potentially all triggered by the one event and to a different standard. Addressing this may require organisations to adopt a “gold standard” approach to compliance.